Let’s Talk About NMap.

Introduction:
So as most of you know, I’m trying to improve my knowledge and skills within Cyber Security.
This week’s blog most talks about a tool that may be considered “simple” however it’s fundamental to identifying vulnerabilities.
Here’s a brief read about nmap.
As always, before we get into this week’s blog post, be sure applaud and share it with your friends.
Happy Reading!
So What Is It?
It’s a network scanning tool that is used widely across industry.
You would use this during the “Reconnaissance” stage (first stage) of the Cyber Attack Life Cycle. The whole purpose of this is to discover potential weaknesses of the system that we might be able to exploit.
How Actually Do We Carry Out an NMap Scan:
First of all, you need to make sure that the nmap tool is installed. I carry out scans on a kali linux VM where nmap is installed my default.
I’ve used ChatGPT to list out the most common installation methods:

Now, back to the actual scan itself:
nmap IP_ADDRESS is the bare minimum command that you need to start an nmap scan. I will show the example response below:
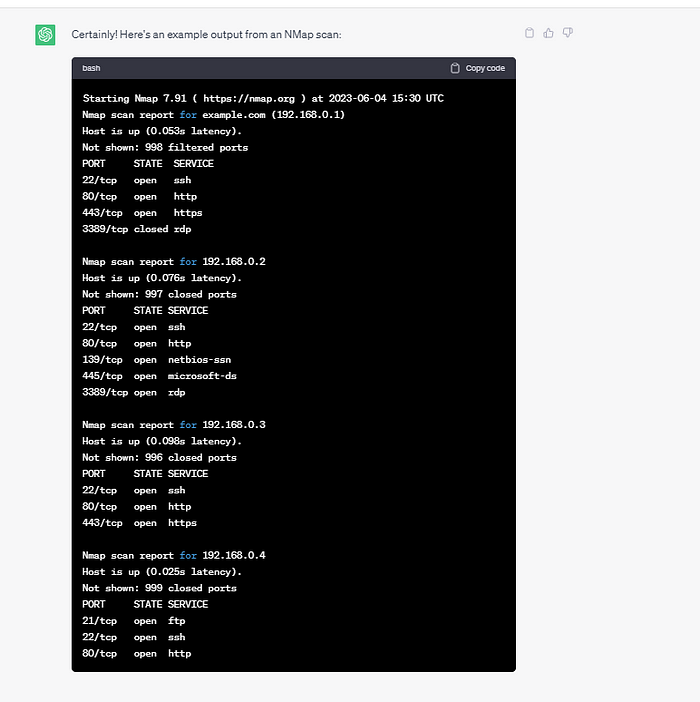
My Experiences:
I’m still quite new to Cyber Security but I’d definitely say that NMap scans are helpful.
They quite literally list out the ports/services that are open. For e.g. if port 80 is shown then I know that pasting the IP address into my web browser will lead to a website being shown.
It’s important to note that I’m still very new to this and that I’m always learning.
Additional Flags:
I’ve shown you the “bare bones” nmap scan but you can (and probably should) add additional flags to the command.
I’ve only listed 2 flags here but there are more.
My “Go-To” Nmap Scan Command:
nmap -sC -sV
- -sC — Allows for use of the Nmap Scripting Engine.
- -sV — Enables version detection during the scan.
I use this for both TryHackMe and HackTheBox as it was recommended by them.
Conclusion:
The Nmap tool is a very handy way to get started with Ethical Hacking.
It makes it easy to scan, detect and break down a system.
Final Things:
As always, thank you for taking the time to read this blog post. It was definitely shorter than normal however I hope that you liked my summary of NMap and I hope that you were able to take something away from this.
